Solved SLC Computer Science 2072
2072(2016)
(Computer fundamentals)
1. Answer the following questions.
a) Define LAN topology. Draw star topology.
Ans: The arrangement or connection pattern of nodes or computers and other devices of the network is called LAN topology.
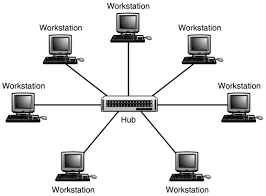
Star Topology
b) Give any two symptoms of virus attacks.
Ans: The symptoms of virus attacks are:
i) Program takes a long time to load.
ii) Corrupting the system’s data.
c) Write one advantage and one disadvantage of multimedia.
Ans: The advantage of multimedia is:
i) It makes teaching learning easier in the classroom.
The disadvantage of multimedia is:
i) Acquisition or rental of equipments to produce multimedia can be costly.
d) Write any two ways of protecting computer software.
Ans: The two ways of protecting computer software are:
i)Password
ii)Backup
e) Write any two services of internet.
Ans: The two services of internet are:
i)E-mail
ii)IRC
2. a)Convert as indicated:
i)(208)10 into Binary
Converting decimal to binary,
2
208
2
104
0
2
52
0
2
26
0
2
13
0
2
6
1
2
3
0
1
1
(208)10=(11010000)2
ii)(104)8 into decimal
Converting octal to decimal,
=1*82+0*81+4*80
=1*64+0*8+4*1
=64+0+4
=68
(104)8=(68)10
b) Perform the binary calculations:
i)1011+1101
1011
 + 1101
+ 110111000
1011+1101=11000
ii)110*11
110
 *11
*11110
+ 110X
10010
110*11=10010
3. Match the following:
Answers:
a) Microwave : Unguided media
b) UTP : Guided media
c) UPS : Power protection device
d) SMTP : Protocol
4. State whether the following statements are true or false:
a) Walky-talky is an example of full duplex mode.
Ans: False
b) Data transfer rate is higher in optical fiber cable than in co-axial cable.
Ans: True
c) The computer security refers to hardware security only.
Ans: False
d) Sound Card is one of the components of multimedia.
Ans:True
5. Write the appropriate technical terms of the following:
a) A program that can disinfect a file from virus.
Ans: Antivirus software
b) A person who steals or destroys other’s data, information, files and program.
Ans: Hacker
c) A company which provides the internet facilities.
Ans: ISP
d) A computer which provides services to other computers in a network.
Ans: Server
6. Write the full forms of:
i)URL :Uniform Resource Locator
ii)HTTP :Hyper Text Transfer Protocol
iii)LAN :Local Area Network
iv)MODEM :Modulator-Demodulator
(Database)
7. Answer the following questions:
a) Write any four data types used in Ms-ACCESS.
Ans: Four data types used in Ms-ACCESS are:
i) Text
ii) Memo
iii) Currency
iv) OLE
b) Define database with example.
Ans: The collection of organized and related information that can be used for different purposes is called database. For example: dictionary and telephone directory.
c) What is query?
Ans: The object of MS-ACCESS that extracts and arranges information from a table is called query.
8. State whether the following statements are true or false:
a) A query is used to select fields and records from only one table.
Ans: False
b) MS-ACCESS is DBMS software.
Ans: True
c) Index decreases the speed of query and sort operations.
Ans: False
d) Data in primary key has to be unique and not null.
Ans: True
9. Match the following:
a) OLE : Data type
b) Validation Rule : Limits the value
c) Form : Data Entry
d) Indexing : Easy to search
( Programming)
10. a) What is procedure?
Ans: The separate block of statements used by the module level code and called by any number of times is called procedure.
b) Write any two data types used in ‘c’ language.
Ans: The two data types used in the ‘c” language are:
i) char
ii) int
c) Write down the functions of the following statements:
i) OPEN: It opens a sequential file for one of the three possible operations i.e. reading, writing or appending.
ii) MKDIR: It makes or creates a new directory on the specified disk.
11. Re-write the following program after correcting the bugs:
FUNCTION SUM(m,n)
Rem to print sum of two numbers
a=6
b=7
DISPLAY SUM(a,b)
END
FUNCTION SUM(m,n)
S=m+n
S=SUM
END SUM
Debugged program:
DECLARE FUNCTION SUM(m,n)
Rem to print sum of two numbers
a=6
b=7
PRINT SUM(a,b)
END
FUNCTION SUM(m,n)
S=m+n
SUM=S
END FUNCTION
12. Write the output of the following program:
DECLARE FUNCTION Interest(p,t,r)
CLS
LET p=100
LET t=2
LET r=5
LET d=Interest(p,t,r)
PRINT “The simple interest=”;d
END
FUNCTION Interest (p,t,r)
Interest=(p*t*r)/100
End FUNCTION
OUTPUT
The simple interest=10
(Error message will be displayed if the sub program is missing.)
13. Study the following program and answer the following questions:
DECLARE FUNCTION Prod(N)
INPUT “Any number”;N
X=Prod(N)
PRINT X
END
FUNCTION Prod(N)
F=1
FOR K=1 TO N
F=F*K
NEXT K
Prod=F
END FUNCTION
a) Write the name of the user defined function used in the above program.
Ans: The name of the user defined function used in the above program is Prod.
b) Name the loop in the above program.
Ans: The loop in the program is FOR…NEXT.
14. a) Write a program using SUB…..END SUB to display reverse of input-string.
DECLARE SUB REV(A$)
CLS
INPUT “ENTER ANY STRING”;A$
CALL REV(A$)
END
SUB REV(A$)
FOR I= LEN(A$) TO 1 STEP -1
B$=MID$(A$,I,1)
W$=W$+B$
NEXT I
PRINT “REVERSED STRING=”W$
END SUB
b) Write a program using FUNCTION…END FUNCTION to find area of the triangle.
DECLARE FUNCTION AREA(B,H)
CLS
INPUT “ENTER BASE”;B
INPUT “ENTER HEIGHT”;H
PRINT “AREA OF TRIANGLE”;AREA(B,H)
END
FUNCTION AREA(B,H)
AREA=(1/2)*B*H
END FUNCTION
c) A sequential data file called “Marks.dat” contains NAME, AGE, CITY, and TELEPHONE fields. Write a program to display all the contents of the data file.
OPEN “Marks.dat” FOR INPUT AS #1
CLS
WHILE NOT EOF(1)
INPUT #1, N$, A, C$, T#
PRINT N$, A, C$, T#
WEND
CLOSE #1
END




